NCBRT/ACE eLearning Courses
The content below is hosted on Moodle and requires a login. Creating an account is simple and provides instant access to course content. Click the Register button to register and access this free training. Course offerings are organized by type: DHS/FEMA Certified Courses, Micro Modules, and Webinars. Some content is also available in Spanish, and is listed separately below.
Note - DHS Certified Courses and Micro Modules are restricted to US Citizens. Non-citizens may apply for access by completing the Foreign National Visitor Access Request form after creating an account.
DHS/FEMA Certified Courses
These training courses are certified by DHS/FEMA and offer a certificate of completion and continuing education units. Participants are required to obtain a FEMA Student ID (SID) prior to enrolling in these courses.
Shopping Center Security Terrorism Awareness Training Program (AWR-304-W)

This course provides security training personnel with increased awareness of the various facets of terrorism and criminal activity that could occur at a retail facility. During this course participants will examine weapons that may be used in a terror attack and will be able to describe various attack tactics that may be used against a retail facility. Participants will also be able to assess potentially suspicious behavior and will be able to conduct surveillance at their facility. The course describes proper response to terrorist or criminal incidents.
Micro Modules
Micro Modules are brief, webinar-formatted presentations based on NCBRT course content. They may be used as review or refresher for users who have previously taken NCBRT training or serve as an introduction to topics for those who have not completed the related course. Certificates of completion are available for each Micro Module.
Internal and External Information Sharing for Campus Safety

The purpose of this micro module is to highlight the importance of information sharing and demonstrate how campuses work with trusted partners to prevent, assess, and respond to potential threats.
Creating a Campus Continuity of Operations Plan

The purpose of this micro module is to introduce the role of a Continuity of Operations Plan (COOP) in helping campuses maintain critical services during emergencies. Participants will explore the seven planning phases and understand how a COOP coordinator and planning team work together to build a strong, actionable plan.
Scales of a Biological Incident

Each biological incident will be different in both scope and severity, or scale. As the number of infectious disease outbreaks continues to grow worldwide, education and preparedness will be crucial in effective responses to such incidents. This presentation explains the terms typically used to describe the varying scales of a biological incident.
The Importance of Planning for an Active Threat Incident

Active threat perpetrators often plan extensively for a campus attack. The best way for the campus community to combat this is through preparation of their own. Disrupting an attacker's plan can significantly influence the outcome by minimizing injuries and deaths. This presentation describes the importance of planning for an active threat and provides sample planning measures.
Three Phases of an Active Threat Incident

This presentation discusses the three phases of an active threat incident: recognition, activation, and resolution. Understanding these phases can help immediate responders, or the people who are immediately on the scene when an active threat incident begins, plan effectively to protect themselves and their community.
Collection Planning

This Micro Module discusses the collection planning framework for intelligence gathering and provides a practical, flexible framework for building an effective intelligence collection plan. In the presentation, we discuss how to build an agency-level collection plan, questions to ask when collection planning, strategies for building a plan, tips for understanding an investigation’s target, and more.
Three Phases of Human Reaction to Disaster

This Micro Module presentation discusses the three phases of human reaction to disaster: denial, deliberation, and the decisive moment. Understanding these phases and training for crisis situation can help individuals progress through the phases more quickly to react efficiently and increase their chances of survival. This presentation was made using information from LSU NCBRT/ACE's PER-374: Active Threats on Campuses: Protective Measures and Response.
Elements of Successful Integration

This Micro Module from LSU NCBRT/ACE describes the elements necessary for successful integration of emergency response disciplines during a threat. These elements include resource management, command and coordination, and communication and information management. This presentation describes each element and the necessary steps to ensure overall effectiveness.
Campus Threat Identification and Risk Assessment (THIRA)

This Micro Module from LSU NCBRT/ACE discusses the Threat Identification and Risk Assessment (THIRA) for campuses to enhance resilience and preparedness planning. The presentation covers the factors campuses should consider when identifying significant threats, how to adapt THIRA to meet a campus’ specific needs, and the steps of the THIRA process.
This presentation was created using content from LSU NCBRT/ACE’s Campus Emergencies: Prevention, Response, and Recovery course. Learn more about this course here.
CBRNE Agents: Types of Harm (TRACEM-P)

In this video, we discuss the TRACEM-P method for categorizing hazards associated with chemical, biological, radiological, nuclear, and explosive (CBRNE) materials or toxic industrial chemicals (TIC). This presentation gives an overview of the types of harm associated with these types of materials and how TRACEM-P can help crime scene investigators categorize risks of an incident for tactical decisions.
Types of Criminal Intelligence

The purpose of this LSU NCBRT presentation is to provide an overview of the three types of criminal intelligence: tactical, operational, and strategic intelligence. This presentation gives definitions and examples of each type of intel and describes when different kinds of criminal intelligence are most useful for law enforcement.
Levels of PPE

This Micro Module addresses types and levels of personal protective equipment, or PPE. Ensuring that responders are wearing the correct PPE for a specific incident is crucial to protect lives and decrease contamination risk. In this presentation, we discuss the four levels of PPE, the types of clothing and gear for each level, and the types of conditions in which to use each type of PPE.
Negotiating Closed Doors

The purpose of this LSU NCBRT presentation is to provide tactically sound techniques for law enforcement to use when negotiating a closed door during an active shooter incident. First responders encounter more closed doors than open doors. Doors may be most likely locked and possibly barricaded. Given the urgency of the situation and the primary focus of stopping the killing, the responder will need to make good decisions on what time is spent negotiating locked doors.
Negotiating Open Doors

The purpose of this LSU NCBRT presentation is to provide tactically sound techniques for law enforcement to use when negotiating an open door during an active shooter incident. When responders determine that they will enter a room, they must quickly and decisively take steps to pass through the door or threshold and be prepared to handle any problem. Properly negotiating a door prior to making entry sets officers up for success by identifying specific tasks to be performed and limiting their exposure to potential threats prior to making entry.
Affirming Learning

The purpose of this LSU NCBRT presentation is to explain the three tasks that are required to affirm learning in the classroom, which are monitoring, assessing, and evaluating. This information is primarily for those tasked with training first responders and others in emergency response related fields. Effective instructors monitor, assess, and evaluate student learning to ensure they attain knowledge and skills specified in the course.
Intentional Biological Incidents

The purpose of this LSU NCBRT presentation is to review the different types of intentional biological incidents. This intentional use of biological agents as weapons can be a biocrime or an act of biowarfare, bioterrorism, or agroterrorism. To induce social disruption, an offender might select a particular biological agent because of its ability to be highly contagious and debilitating. Intentional incidents may involve a wide area of exposure at one time or exposure at multiple locations.
Types of Biological Incidents

The purpose of this LSU NCBRT presentation is to explain the different types of biological incidents. Emergency responders, law enforcement, and public health officials should be aware of the implications and consequences of biological incidents—whether natural, accidental, or intentional. Law enforcement plays a critical role and should be involved early in a response to a biological incident so that critical evidence is not lost in the event that a crime has been committed. Understanding these incidents enables a comprehensive and effective response, highlighting the importance of cooperation among various agencies to safeguard public health and security.
Types of Biological Agents
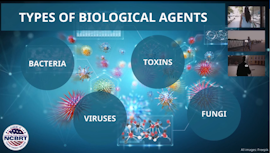
The purpose of this LSU NCBRT presentation is to provide an overview of the types of biological agents that may be present during a domestic biological incident. Responders may be involved in response to biological incidents. Knowing if an organism is bacterial, viral, fungal, or resulting from a toxin can greatly impact response actions. This information is key both to protecting responders and to preventing further illness in the community.
Attacker Characteristics

The purpose of this LSU NCBRT/ACE presentation is to provide an overview of observable attacker characteristics that may indicate an attack is part of a larger incident and a potential Complex Coordinated Terrorist Attack (or CCTA). There are several observable characteristics that may also include plans to overwhelm resources and make the attack as effective as possible. Recognition of these clues early in the attack will allow responders to activate appropriate assets and employ response resources as efficiently as possible.
Biological Agents: Routes of Exposure

This LSU NCBRT presentation provides an overview of the major routes of entry for biological agents into the body. The most common routes of exposure are ingestion, injection, absorption, and inhalation. Specific examples of each are provided.
Suspicious Activity Reports

This LSU NCBRT presentation provides participants with an overview of the fundamentals of Suspicious Activity Reports (SARs). The Information Sharing Environment (ISE) is the platform on which the National Terrorism Information Sharing and Suspicious Activity Reporting (SAR) initiatives are managed. A suspicious activity is an observed behavior reasonably indicative of preoperational planning related to terrorism or other criminal activity. It is critical for agencies to share collected information. SARs record suspicious activities that need further inquiry and follow-up.
Door Barricading

The purpose of this presentation is to provide demonstrations of effective door barricading techniques. During an active threat incident, it is important for individuals to place as many obstacles and time-consuming barriers between themselves and the threat as possible. Taking steps to impede or stop the progress of a threat could increase survivability and save lives. Participants are encouraged to apply principles from this course to plans and procedures in their workplaces.
Consolidating Training Needs

The purpose of this presentation is to illustrate the benefits of consolidating training needs into a jurisdictional multiyear training plan. This plan provides opportunities for interagency collaboration and training. It allows jurisdictions to train with other agencies or jurisdictions that will be responding during an emergency. Consolidating several agencies’ needs into one jurisdiction-wide training plan allows agencies with common training goals to work together, share resources, and provide each other with help and support. Multidisciplinary training can lead to a better-informed, better-connected response community, and a far more successful response.
Assessment Team Check-Up

The purpose of this presentation is to teach emergency planners how to ensure that their training assessment team includes members that adequately represent the jurisdiction. Team members from the whole community will be responsible for completing the assessment process. The team will analyze response capabilities to identify training needs, develop training goals for the jurisdiction, identify training sources, and create a multiyear training plan.
Preparedness Tools

The purpose of this presentation is to provide an overview of the documents that planning teams should refer to when completing a readiness assessment. By evaluating their abilities to meet their emergency operations plan (EOP) using traditional and national preparedness tools, participants learn that agencies that plan and train together are much better equipped to successfully respond together.
Behavior Considerations for Document Inspection

The purpose of this presentation is to review some of the behavioral considerations for the inspection of identity documentation. This course provides participants with the skills to evaluate the authenticity of identification documents and ensure that documents are lawfully possessed. This course provides a professional and comprehensive examination of overt and covert security features of genuine current state drivers licenses and federal travel documents. It also provides tools and techniques that participants can use during the interview process to identify imposters and to examine identification documents that subjects present to them.
Refreshing Your Jurisdictional Profile

The purpose of this presentation is to provide guidance on how emergency planners can understand and enhance their jurisdictional profiles. Constantly changing communities must plan for threats and their associated needs must be consistently and continuously reviewed. Response communities, resource groups, and critical infrastructure must also be identified within the established geographic region.
Document Inspection Process

The purpose of this presentation is to review the process and considerations for the inspection of identity documentation. This course provides participants with the skills to evaluate the authenticity of identification documents and ensure that documents are lawfully possessed. It also provides tools and techniques that participants can use during the interview process to identify imposters and to examine identification documents that subjects present to them.
Overview of the RTIPP Process

The purpose of this presentation is to provide an overview of the seven steps in the Readiness: Training Identification and Preparedness Planning process. The RTIPP process assists jurisdictions efficiently plan and schedule training that is relevant to community preparedness. It is critical that agencies within a jurisdiction plan and train together so they can respond effectively when an incident occurs. In an all hazards, whole community approach, public sector agencies, private sector organizations, and nongovernmental organizations all play a role in preparedness.
Communicating Risk Effectively in a Food Emergency

The purpose of this presentation is to provide an overview of risk communication and the guidelines and strategies for developing effective risk communication in a food emergency.
Staging in an Active Shooter Incident

The purpose of this presentation is to provide a focused overview of staging and staging concepts for all responders as well as law enforcement. It also provides tactical approach, tools, and resource considerations for a response attributed to an intentional act by individuals that creates or evolves into an active shooter incident or complex coordinated attack (CCA).
Mechanical Breaching

The purpose of this presentation is to provide examples of mechanical breaching for law enforcement. The video will review methods of mechanical breaching including: forcing, cutting and crushing or breaking.
Consideration for Breaching

The purpose of this presentation is to provide an informational introduction for basic considerations during breaching for law enforcement officers. The content reviews entry points and mechanical breaching tools.
Tables and Chairs: Setting Up An Incident Command Post

The purpose of this presentation is to provide participants one example of physically establishing an incident command post (ICP). During an emergency, it is critical for individuals to know their various roles and responsibilities as well as how information should flow within the ICP.
Building Emergency Action Plans (BEAPs)

The purpose of this presentation is to provide an informational introduction for Building Emergency Action Plans, or BEAPs. A BEAP details emergency actions at the building level, including occupant actions and should support an Emergency Operations Plan.
Behavioral Intervention Teams (BITs)

The purpose of this presentation is to provide an informational reminder of key principles for Behavioral Intervention Teams. BITs are formed to respond to the early detection of and intervention of worrisome or potentially harmful behavior and to prevent campus violence. These BITs provide a centralized point to which concerned members of the campus community can report instances of worrisome or potentially harmful behavior.
Introduction to Emergency Operations Plans

The purpose of this presentation is to provide an informational introduction for Emergency Operating Plans, or EOPs. An EOP serves as the cornerstone of preparedness and emergency activities of a campus. This presentation provides resources for campuses to begin developing their EOPs.This presentation was created using content from NCBRT's PER-340, Active Threat Integrated Response Course.
Pressure Points

The Pressure Points video illustrates how to use pressure points in controlling severe bleeding as a first step before tourniquet application or wound packing occurs.
BATH Assessments

The LSU NCBRT/ACE BATH Assessments presentation is part of a series of micro modules based on certified course content. The purpose of this presentation is to provide emergency responders an overview or refresher of key principles for BATH Assessments. Using this simple assessment tool, responders identify and treat life-threatening bleeding, maintain an open airway, monitor for signs of tension pneumothorax, and attempt to maintain the victim’s body temperature to prevent hypothermia. This presentation was created using content from NCBRT's PER-340, Active Threat Integrated Response Course.
Negotiating Doors

This presentation provides emergency responders an overview or refresher of key principles for negotiating open and closed doors as they clear rooms during an active threat situation. When responders make room entries, they must move quickly and decisively through the door and prepare to engage the threat.
Wound Packing

The purpose of this video presentation is to provide emergency responders an overview or refresher of key principles of wound packing. Wound packing is performed during the indirect threat care phase of an incident when there is no active threat. It may be used to control severe bleeding in places where tourniquets are not effective, such as bleeding near the junction of the torso and a limb.
Movement to Contact

The Movement to Contact micro module provides emergency responders an overview or refresher of key principles for team movement as they move to mitigate an active threat. This presentation looks at team sizes and configurations, as well as the advantages and disadvantages of a few common ones.
Direct Threat Care - Tourniquets

The purpose of this presentation is to remind Emergency Responders of key tourniquet application principles in a direct threat care environment.
Zones of Operation During an Active Threat
Zones of operation are defined by the relative level of threat. These designations determine where certain actions and specific personnel are allowed to operate. As a result, and for a safer and more efficient response, we identify and label areas at the scene based on our knowledge of the potential threat(s) in each of those areas. We do this by assigning identifiers: the hot zone, the areas of highest risk; the warm zone, an area of intermediate risk; and the cold zone, areas of least risk with regard to the incident. This presentation was created using content from NCBRT’s PER-340, Active Threat Integrated Response Course.
Direct Pressure

The purpose of this presentation is to remind emergency responders of key principles for applying direct pressure to injuries sustained during an active threat incident when tourniquets may not be an option. This presentation was created using content from NCBRT’s PER-340, Active Threat Integrated Response Course.
Rescue Task Force Formations

The purpose of this presentation is to provide Emergency Responders an informational reminder of key principles surrounding the formation and response of a Rescue Task Force (RTF) in an active shooter or active threat incident. This presentation was created using content from NCBRT’s PER-275, Law Enforcement Active Shooter Emergency Response, and PER-340, Active Threat Integrated Response Course.
Contact Team Principles and Priorities

This presentation will address contact team concepts, principles, and priorities. These include solo officer entries, bypassing the wounded, and directing follow-on responders. This presentation was created using content from NCBRT’s PER-275, Law Enforcement Active Shooter Emergency Response, and PER-340, Active Threat Integrated Response Course.
CAN and SIM

The purpose of this presentation is to remind Emergency Responders of key principles of CAN (Conditions, Actions, and Needs) reports, and using SIM (Security, Immediate Action Plan, Medical Intervention) during an active threat incident. These principles can assist first responders to identify needs and rapidly respond to active threat incidents. This presentation was created using content from NCBRT’s PER-335, Critical Decision Making for Complex Coordinated Attacks, and PER-340, Active Threat Integrated Response Course.
Webinars
Webinars are short training videos to provide instruction on specific topics. Certificates of completion are available for each webinar.
Fourth Generation Nerve Agents

This video provides the viewer information regarding fourth generation nerve agents (FGA). After viewing, you will understand FGA mechanisms of toxicity, signs and symptoms of FGA poisoning, medical countermeasures, and immediate protective actions to prevent further contamination.
Micro Modules en Español
Micro Modules are brief, webinar-formatted presentations based on NCBRT course content. They may be used as review or refresher for users who have previously taken NCBRT training or serve as an introduction to topics for those who have not completed the related course. Certificates of completion are available for each Micro Module.
Taponamiento de Heridas

El propósito de esta presentación en video es brindar a los servicios de emergencia una descripción general o un repaso de los principios clave del Taponamiento de heridas. El taponamiento de heridas se realiza durante la fase de atención de amenazas indirectas de un incidente cuando no hay una amenaza activa. Puede usarse para controlar el sangrado severo en lugares donde los torniquetes no son efectivos, como el sangrado cerca de la unión del torso y una extremidad.
Negociar Puertas

Esta presentación proporciona a los servicios de emergencia una descripción general o un repaso de los principios clave para negociar puertas abiertas y cerradas mientras limpian las habitaciones durante una situación de amenaza activa. Cuando los socorristas ingresan a la habitación, deben moverse rápida y decisivamente a través de la puerta y prepararse para enfrentar la amenaza.
Movimiento Para Hacer Contacto

El micro módulo Movimiento para hacer contacto proporciona a los servicios de emergencia una descripción general o un repaso de los principios clave para el movimiento del equipo a medida que avanzan para mitigar una amenaza activa. Esta presentación analiza los tamaños y configuraciones de los equipos, así como las ventajas y desventajas de algunos de los más comunes.
Formaciones de equipos de rescate

El propósito de esta presentación es proporcionar al personal de respuesta a emergencias un recordatorio informativo de los principios clave que rodean la formación y respuesta de un Grupo de trabajo de rescate (RTF) en un incidente de tirador activo o amenaza activa. Esta presentación se creó utilizando contenido de PER-275 de NCBRT, Respuesta de emergencia de tirador activo de aplicación de la ley, y PER-340, Curso de respuesta integrada a amenazas activas.
Zonas de Operacion Durante una Amenaza Activa

Las zonas de operación se definen por el nivel relativo de amenaza. Estas designaciones determinan dónde se permite operar ciertas acciones y personal específico. Como resultado, y para una respuesta más segura y eficiente, identificamos y etiquetamos áreas en la escena en base a nuestro conocimiento de las amenazas potenciales en cada una de esas áreas. Hacemos esto asignando identificadores: la zona caliente, las áreas de mayor riesgo; la zona cálida, zona de riesgo intermedio; y la zona fría, áreas de menor riesgo con respecto al incidente. Esta presentación se creó utilizando contenido del PER-340, Curso de respuesta integrada a amenazas activas de NCBRT.
Atención de Amenaza Directa Aplicación de Torniquete

El propósito de esta presentación es para recordarle al personal de respuesta a emergencias los principios clave de la aplicación de torniquetes en un entorno de atención directa a amenazas.
Presión Directa

El propósito de esta presentación es recordarle a los servicios de emergencia los principios clave para aplicar presión directa a las lesiones sufridas durante un incidente de amenaza activa cuando los torniquetes pueden que no sean una opción. Esta presentación se creó utilizando contenido del PER-340, Curso de respuesta integrada a amenazas activas de NCBRT.
Principios Y Prioridades del Equipo de Contacto

Esta presentación abordará los conceptos, principios y prioridades del equipo de contacto. Estos incluyen entradas de oficiales en solitario, evitando a los heridos y dirigiendo a los respondedores de seguimiento. Esta presentación se creó utilizando contenido de PER-275 de NCBRT, Respuesta de emergencia de tirador activo de aplicación de la ley, y PER-340, Curso de respuesta integrada a amenazas activas.
CAN Y SIM

El propósito de esta presentación es recordarle al personal de respuesta a emergencias los principios clave de los informes CAN (Condiciones, Acciones y Necesidades) y el uso de SIM (Seguridad, plan de acción Inmediata, intervención Médica) durante un incidente de amenaza activa. Estos principios pueden ayudar a los socorristas a identificar necesidades y responder rápidamente a incidentes de amenazas activas. Esta presentación se creó utilizando contenido del PER-335 de NCBRT, Toma de decisiones críticas para ataques coordinados complejos, y PER-340, Curso de respuesta integrada a amenazas activas.